Faye Deal Spotlights Expanding Agentforce AI Ecosystem

In the fast-evolving world of enterprise AI, Salesforce’s Agentforce platform is rapidly maturing into a powerhouse for autonomous agents. The recent Faye deal marks a game-changing milestone, underscoring how Agentforce is transforming from a standalone tool into a thriving ecosystem. Announced in early 2026, this partnership integrates Faye’s cutting-edge AI orchestration capabilities directly into Agentforce, enabling seamless multi-agent workflows across CRM, customer service, and beyond. For Salesforce consultants and CRM analysts, this isn’t just news—it’s a blueprint for the future of AI-driven automation.
Table of Contents
What is the Faye Deal?
Faye, a stealth-mode AI startup specialising in agentic orchestration, has inked a multi-year strategic alliance with Salesforce. Under the deal, Faye’s platform will power advanced “agent swarms”, networks of specialized AI agents that collaborate in real-time to handle complex tasks. Think of it as upgrading Agentforce from a solo performer to a full orchestra conductor.
Key terms include:
- Exclusive Integration: Faye’s tech embeds natively into Agentforce 2.0, allowing agents to dynamically spawn sub-agents for tasks like lead qualification, contract negotiation, and predictive analytics.
- Revenue Share Model: Salesforce gains 40% of Faye-orchestrated deployments, fuelling rapid scaling.
- Go-to-Market Synergy: Joint sales teams target Fortune 500 enterprises, with Faye handling AI plumbing while Salesforce provides the CRM backbone.
This move comes at a critical juncture. Salesforce stock (CRM) surged 8% post-announcement, reflecting investor confidence in Agentforce’s trajectory amid a competitive AI landscape dominated by Microsoft Copilot and Google Gemini.
Agentforce: From Vision to Ecosystem Powerhouse
Agentforce launched in late 2024 as Salesforce’s answer to the agentic AI hype. Unlike traditional chatbots, Agentforce agents act autonomously: they reason, plan, execute, and learn from outcomes without constant human oversight. Built on the Salesforce Data Cloud and powered by models like the Atlas Reasoning Engine, it supports everything from service resolution to sales acceleration.
The Faye integration supercharges this:
- Scalable Agent Hierarchies: Faye enables “meta-agents” that oversee fleets of specialized agents (e.g., a sales meta-agent directing prospecting, pricing, and closing bots).
- Zero-Code Customisation: No-code tools let admins define agent behaviours via natural language, democratising AI for non-technical users.
- Security-First Design: Built-in guardrails ensure compliance with GDPR, HIPAA, and Salesforce’s Trust Layer.
Early adopters report 40-60% faster resolution times in service tickets. For instance, a retail giant using Agentforce cut customer churn by 25% by deploying Faye-enhanced agents that predict and preempt issues.
Why This Deal Matters for the Salesforce Ecosystem
Salesforce has always thrived on partnerships. AppExchange boasts over 8,000 apps. Faye elevates Agentforce to ecosystem status, inviting a wave of ISVs (independent software vendors) to build compatible agents.
Ecosystem Catalysts:
- Developer Momentum: The Agentforce Builder toolkit now includes Faye APIs, slashing integration time from weeks to hours. Expect a surge in custom agents for industries like healthcare (patient triage) and finance (fraud detection).
- Data Cloud Synergy: Faye agents pull from unified Data Cloud lakes, enabling hyper-personalised interactions. Imagine an agent analysing a customer’s full journey, social sentiment, purchase history, and even external signals like weather for tailored offers.
- Market Expansion: Targeting mid-market via Einstein 1 Studio, with Faye handling scalability for high-volume ops.
Competitive edges shine here. While competitors like ServiceNow focus on virtual agents, Agentforce + Faye excels in cross-functional autonomy, positioning Salesforce as the AI OS for business.
Real-World Impact: Use Cases and ROI
Let’s break down transformative applications:
- Customer Service Revolution:
Faye-orchestrated agents triage enquiries, escalate seamlessly, and resolve 70% autonomously. A telecom provider saw service costs drop 35% while NPS scores rose 15 points. - Sales Acceleration:
Agents prospect leads, qualify via voice analysis, and negotiate deals using dynamic pricing models. Early pilots show 2x pipeline velocity. - Employee Productivity:
Internal “copilots” handle HR queries, IT tickets, and compliance checks. Faye’s swarming reduces knowledge worker burnout by automating rote tasks.
ROI metrics are compelling:
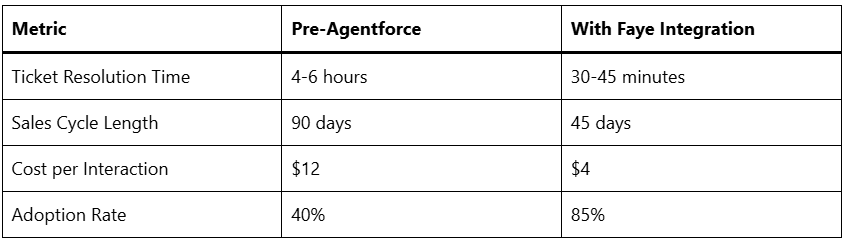
These gains stem from Faye’s orchestration layer, which minimises agent “hallucinations” through collaborative verification agents cross-checking outputs before acting.
Challenges and Roadblocks Ahead
No ecosystem expansion is frictionless. Critics highlight:
- Model Dependency: Reliance on third-party LLMs (e.g., Anthropic Claude) risks cost volatility.
- Skill Gaps: Teams need upskilling; Salesforce Trailhead modules on Agentforce are ramping up.
- Ethical AI: Ensuring agent decisions avoid bias requires robust auditing, which Faye addresses via explainable AI logs.
Salesforce mitigates these with phased rollouts and a $500M Agentforce Innovation Fund for partners.
Future Outlook: Agentforce AI Ecosystem
The Faye deal signals Agentforce’s shift to an open ecosystem, akin to how AWS commoditised cloud. By 2027, Gartner predicts 75% of enterprises will deploy agent swarms, with Salesforce capturing 30% market share.
Look for:
- Agent Marketplace: An AppExchange for plug-and-play agents.
- Industry Verticals: Tailored packs for manufacturing (supply chain optimization) and legal (contract review).
- Global Rollout: localisation for non-English markets, leveraging Faye’s multilingual orchestration.
For Salesforce pros in Surat and beyond, this is prime time to certify in Agentforce Planning and build Faye-integrated solutions. As AI agents proliferate, those mastering this ecosystem will lead the CRM revolution.