Why Ignoring DevOps Security in Salesforce Is Risky

Introduction
Salesforce is a powerful Customer Relationship Management (CRM) platform that helps businesses streamline operations, enhance customer engagement, and drive growth. However, as organizations increasingly adopt DevOps practices to accelerate Salesforce deployments, security often takes a backseat. Ignoring security in Salesforce DevOps can lead to data breaches, compliance violations, and reputational damage.
This blog explores why DevOps security in Salesforce is critical, the risks of neglecting it, and best practices to ensure a secure DevOps pipeline.
Table of Contents
1. Understanding DevOps in Salesforce
What Is Salesforce DevOps?
Salesforce DevOps refers to the integration of development (Dev) and operations (Ops) to automate and streamline the software delivery lifecycle. It includes:
- Version Control (Git, Bitbucket)
- Continuous Integration/Continuous Deployment (CI/CD)
- Automated Testing
- Environment Management
- Monitoring & Compliance
Why DevOps Security Matters
Security in DevOps (DevSecOps) ensures that security is embedded at every stage code development, testing, deployment, and monitoring. Ignoring security can lead to:
- Unauthorized access to sensitive data
- Malicious code injections
- Compliance failures (GDPR, HIPAA, SOX)
- System downtime & financial losses
2. Key Security Risks of Ignoring DevOps in Salesforce
A. Data Breaches & Leaks
Salesforce stores customer data, financial records, and business insights. A weak DevOps pipeline can expose vulnerabilities like:
- Hardcoded credentials in metadata or scripts
- Misconfigured permissions leading to unauthorized access
- Unsecured APIs allowing hackers to extract data
Example: A misconfigured Salesforce Connected App could expose OAuth tokens, allowing attackers to impersonate users.
B. Compliance Violations
Many industries have strict regulations (GDPR, CCPA, HIPAA). Poor DevOps security can result in:
- Audit failures due to lack of change logs
- Unauthorized changes violating compliance policies
- Insufficient data encryption leading to legal penalties
C. Malicious Code Deployments
Without proper security checks, attackers can:
- Inject malicious scripts into Salesforce orgs
- Deploy backdoors through unverified packages.
- Exploit vulnerabilities in third-party integrations
Example: A developer unknowingly pushes a vulnerable Apex class, allowing a hacker to execute SOQL injection attacks.
D. Environment Sprawl & Shadow IT
Uncontrolled DevOps practices can lead to:
- Unauthorized sandbox copies containing production data
- Unmanaged changes bypassing security reviews
- Shadow IT deployments (e.g., unsanctioned AppExchange apps)
E. Insider Threats & Human Error
Even trusted employees can cause security risks:
- Accidental data exposure (e.g., sharing a backup file publicly)
- Privilege misuse (e.g., granting excessive permissions)
- Lack of rollback mechanisms leading to irreversible damage
3. Best Practices for Secure Salesforce DevOps
A. Implement Role-Based Access Control (RBAC).
- Least privilege principle: Grant only necessary permissions.
- Separate duties: Developers ≠ Deployers ≠ Admins
- Monitor user activity: Use Salesforce Shield or Event Monitoring.
B. Secure CI/CD Pipelines
- Static Application Security Testing (SAST): Scan Apex, Lightning, and Flows for vulnerabilities.
- Dynamic Application Security Testing (DAST): Test running environments for security flaws.
- Secrets Management: Never store passwords in plaintext; use Azure Key Vault or AWS Secrets Manager.
C. Enforce Change Management Policies
- Mandatory peer reviews before deployment
- Automated approval workflows for production changes
- Comprehensive audit logs for all deployments
D. Encrypt Sensitive Data
- Field-level encryption for PII (personally identifiable information)
- TLS 1.2+ for data in transit
- Salesforce Shield Platform Encryption for data at rest
E. Monitor & Respond to Threats
- Real-time alerts for suspicious activities (failed logins, mass data exports)
- Automated incident response (e.g., revoke access on breach detection)
- Regular penetration testing to identify vulnerabilities
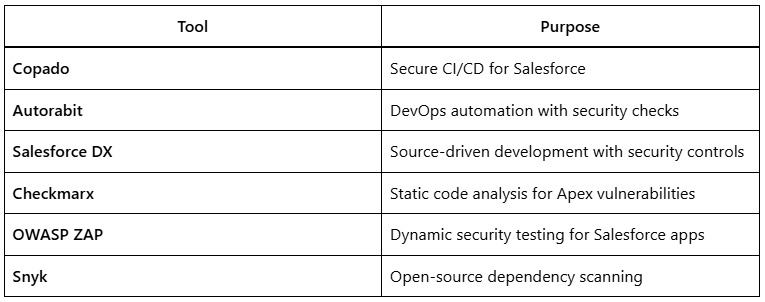
4. Tools for Salesforce DevOps Security
5. My Takeaway: DevOps Security in Salesforce is Risky
Neglecting DevOps security in Salesforce can lead to serious consequences, including data leaks, compliance violations, and system downtime. As Salesforce environments grow more complex, so do the security threats. Integrating security into every phase of the DevOps cycle from development to deployment is no longer optional. It’s a critical step to protect your data, users, and reputation. By prioritizing DevOps security, organizations can ensure a secure, scalable, and compliant Salesforce ecosystem that supports long-term success.

